All Network Identity Manager configuration options can be accessed via the Options menu. The available configuration panels are:
General: General application options for NetIDMgr.
Appearance: Allows you to set the font used by NetIDMgr.
Identities: Default settings for all identities and settings for each identity. Details below.
Notifications: Notification and timer options. NetIDMgr can issue warnings when credentials are about to expire. This configuration panel allows you to set the thresholds at which these warnings are issued. For example, if the warning timeout is set for 10 minutes, NetIDMgr will issue a warning 10 minutes before a credential expires.
The panel also allows you to control the credentials renew timer. If the timer is disabled, NetIDMgr will not automatically attempt to renew credentials. If the Renew at half life intervals when possible option is set, then the timer will expire after the credential has less than half its lifetime left. If the renewal operation fails, it will attempt another renwal after half of the remaining liftime is over (i.e. when the credential has less than 1/4 of its original lifetime left) and so on.
Plug-ins: Enable/disable and check the status of registered plug-ins. Enabling or disabling a plug-in only takes effect after a restart of NetIDMgr.
Kerberos v5: Kerberos v5 Credential Provider Configuration
Kerberos v4: Kerberos v4 Credential Provider Configuration
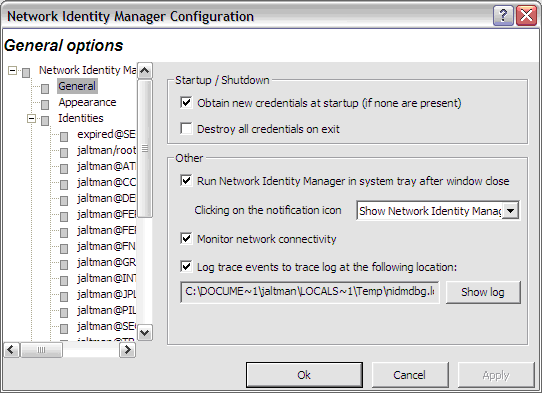
The General options dialog, accessed via the Options menu, allows you to configure operational properties specific to the NetIdMgr application.

The Obtain new credentials at startup (if none are present) checkbox will determine whether or not NetIdMgr will display the New Credentials dialog at startup when no valid credentials exist.
The Destroy all credentials on exit option can be used to empty all of the credential caches when the NetIdMgr is terminated.
The Run NetIdMgr in taskbar notification area after window close checkbox determines the behavior of the window close button. When checked, NetIdMgr will close the window but will continue running and can be accessed from the taskbar notification area. When unchecked, NetIdMgr will behave as if File->Exit was selected from the menu.
Clicking on the notification icon can be configured to either Show Network Identity Manager or Obtain New Credentials. This option controls which menu item on the notification icon menu is the default action.
The Monitor network connectivity option determines whether or not NetIdMgr monitors the configuration of IP addresses on the machine. When IP addresses are added or removed and this feature is activated, the NetIdMgr will probe the identity management servers (e.g., Kerberos Key Distribution Centers) to determine if they are reachable and if so will automatically obtain credentials.
The Log trace events to trace log at the following location option is used to activate a log file that can be used to help debug the behavior of NetIdMgr and its plug-ins. Press the Show log button to view the log file in Windows Notepad.
The Appearance Options page can be used to select an alternate typeface to be used when displaying credentials in the NetIdMgr.
The Identities configuration panel allows you to set the defaults that will be used for all identities. However, most of the settings displayed here can be overridden with specific per-identity settings.
The panel will have a number of sub panels (or tabs) corresponding to each plug-in that maintains per-identity configuration.
A list of identities for which configuration information is maintained will be shown under the main Identities configuration panel name. Each of these correspond to a per identity configuration panel.
Note that adding or removing an identity in the configuration panel only has the effect of adding or removing the identity to or from the list of identities for which configuration information is maintained.
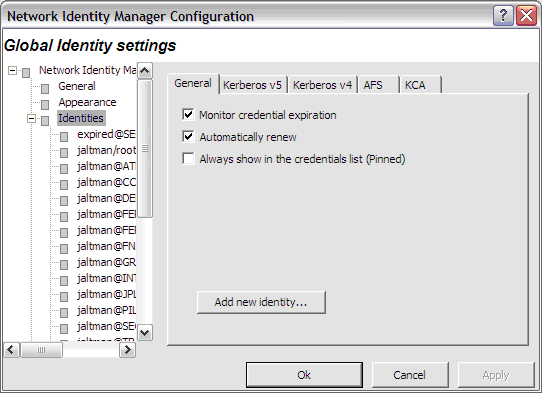
There are three general settings that can be used to set global defaults.
The Monitor credential expiration setting determines whether or not NetIdMgr should monitor the credential lifetimes and issue expiration notifications. This value is used as the default for all new identities.
The Automatically renew setting determines if renewable credentials are automatically renewed prior to expiration. This value is used as the default for all new identities.
The Always show in the credentials list (Pinned) setting determines whether new identities are always pinned within the credentials list. A pinned identity will always be displayed regardless of whether or not there are credentials associated with it.
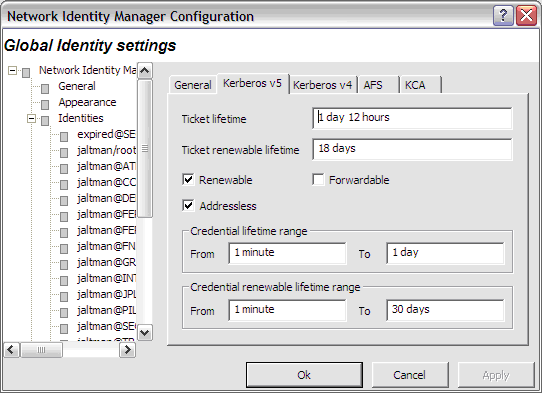
The global Kerberos v5 settings define default credential lifetimes and minimum and maximum values for use in constructing the slider controls used to set the lifetimes.
There are two expiration times associated with Kerberos tickets. The first specifies the length of the time period during which the tickets are valid for use. The second specifies the length of the renewable lifetime. Valid Kerberos tickets may have their valid use lifetime repeatedly extended up until the renewable lifetime expires. The settings on this page are used to configure default lifetime values for NetIdMgr to use when requesting Kerberos tickets from the Kerberos server (key distribution center). The Kerberos server may issue tickets with shorter lifetimes than were requested.
The Renewable, Forwardable, and Addressless options determine whether or not new identities default to obtaining Kerberos v5 tickets with these options.
When Forwardable tickets are received from the Kerberos Server, these tickets can be forwarded to a remote host when you connect via telnet, ssh, ftp, rlogin, or similar applications. When tickets are forwarded, there is no need to obtain Kerberos tickets again to access Kerberized services on the remote host. Forwardable tickets are often required when authenticating to a remote host using ssh or ftp when the remote host requires the ability to authenticate to a remote file system such as AFS.
When Renewable tickets are received from the Kerberos Server, the ticket lifetimes may be renewed without prompting the user for her password. This allows Kerberos tickets to be issued with short lifetimes allowing compromised accounts to be disabled on short notice without requiring the user to enter a password every few hours. When combined with Automatic Ticket Renewal, NetIdMgr can maintain valid tickets for a week, a month, or longer by automatically renewing tickets prior to their expiration. The ability to renew tickets without a password is limited by the ticketís renewable lifetime as issued by the Kerberos Server.
When Addressless is selected, the tickets do not contain IP address information. This enables the tickets to be used from behind Network Address Translators which are frequently found in Cable and DSL Modems.
The minimum and maximum ranges are used by the ticket initialization dialog box when constructing the Lifetime and Renewable Lifetime sliders. These sliders can be used to modify the requested ticket lifetimes when Kerberos tickets are initialized.
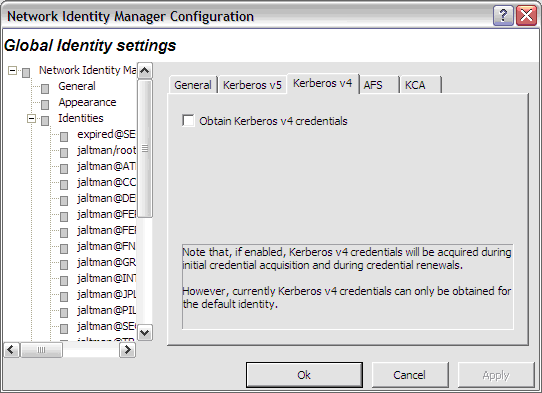
When the Obtain Kerberos v4 credentials button is checked, NetIdMgr will attempt to retrieve Kerberos v4 credentials when ticket initialization, renewal, or importation is performed. Kerberos realms are increasingly configured to support only Kerberos v5 (e.g., Windows Active Directory Domains.) If the realms you use do not support Kerberos v4 it is suggested that this button be unchecked.
Be aware that only the default identity can obtain Kerberos v4 credentials. This limitation is due to the inability of Kerberos v4 applications on Microsoft Windows to specify a credentials cache.
You can access the per-identity configuration panel for a specific identity by selecting the identity name from the list of configuration panels in the configuration dialog.
These panels are similar to the Identities configuration panel, but they change per-identity settings. Changes you make in these panels will override the defaults set in the Identities panel.
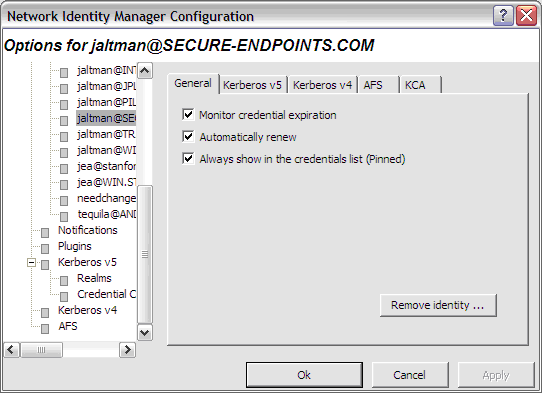
The General page contains a Remove Identity button that can be used to delete this Identity from the Network Identity Manager.
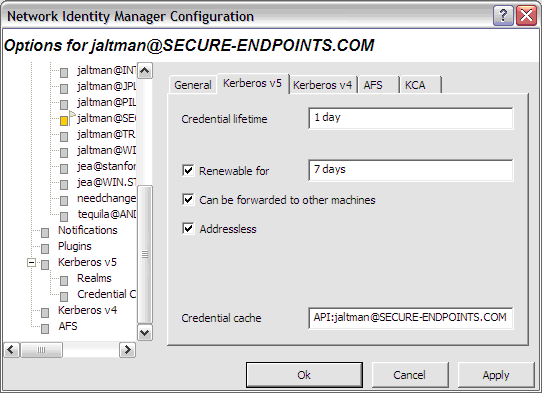
The Kerberos v5 page displays the name of the credential cache currently associated with the Identity.
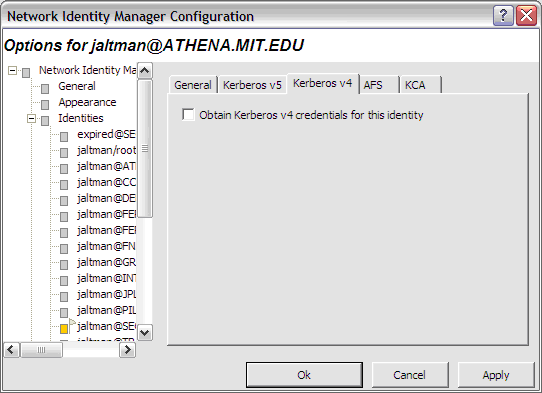
The Kerberos v4 page is optional and may not appear on all systems. Only one identity can obtain Kerberos v4 credentials at a time.
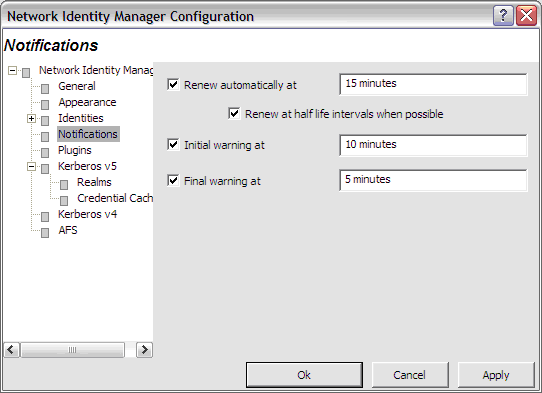
The Renew automatically at check box determines whether or not renewable tickets will be renewed by NetIdMgr when they reach the specified time remaining.
The Initial warning at check box determines whether or not a warning will be issued when the specified time remaining is reached.
The Final warning at check box determines whether or not a warning will be issued when the specified time remaining is reached.
Notifications are performed in two ways. First, icons are displayed next to the affected credentials in the flags column of the display. Second, a balloon tip is displayed off of the NetIdMgr taskbar notification area icon.
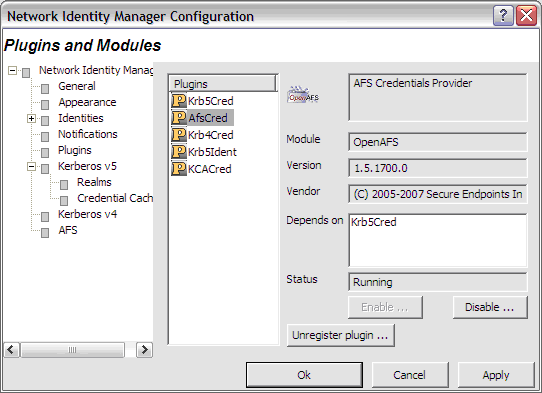
The Plug-ins and Modules page provides status information on the currently loaded plug-ins and modules include a description of their purpose; whether or not it was loaded properly; which other modules are required; and what organization developed it.
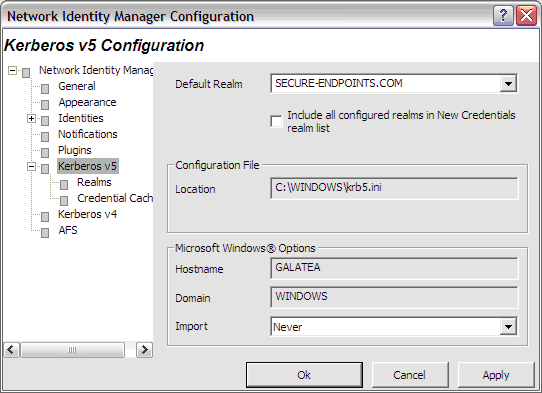
The Kerberos v5 Configuration tab allows you to alter the behavior of the Kerberos v5 identity provider.
In the Default Realm field, select a Kerberos realm from the dropdown list.
The Include all configured realms in New Credentials realm list determines whether all of the realms declared in the Kerberos v5 Configuration file are included in the realms list of the Obtain New Credentials dialog. If disabled, only the realms previously used to obtain credentials are displayed.
The Configuration File field displays the path to the Kerberos v5 configuration file, krb5.ini.
The field labeled Host Name displays the name of your local machine. The Domain Name field displays the domain to which your local machine currently belongs.
The Import Tickets listbox allows you to configure how NetIdMgr interacts with the Microsoft Kerberos Authentication Provider. NetIdMgr will automatically import Kerberos Tickets from the Microsoft LSA at startup depending upon the selected option and whether or not the Kerberos Authentication Provider was used for Windows Logon authorization.
When the Windows Logon identity is imported and is configured as the default identity, the MIT credential cache will be used in preference to the MSLSA credential cache.
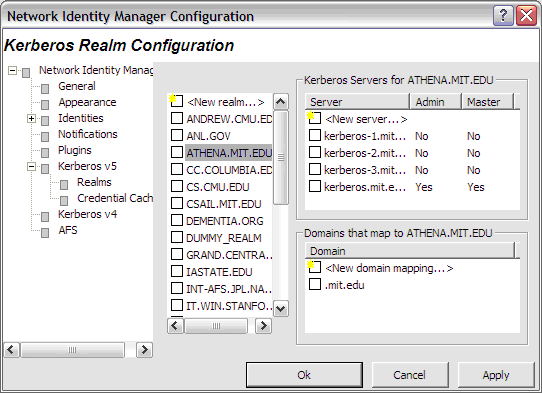
The Kerberos Realm Configuration dialog can be used to manage the contents of the [Realms] and [Domain_Realm] sections of the Kerberos v5 configuration file.

Here, you can specify the name of the in-memory cache used to store the Kerberos v4 tickets. The format of the name is ďAPI:Ē followed by the cache name. Disk caches are not supported by Kerberos for Windows.
The paths to the Kerberos v4 configuration files: krb.con and krbrealm.con may be viewed from this dialog. The default is to store the configuration files in the Windows directory.